Over 900k users were hit by malicious Chrome extensions posing as ChatGPT and DeepSeek tools. We dive deep into the analysis, the C2 exfiltration, and how to secure your browser....

Over 900k users were hit by malicious Chrome extensions posing as ChatGPT and DeepSeek tools. We dive deep into the analysis, the C2 exfiltration, and how to secure your browser....
adb stands for Android Debug Bridge by which you can get root access to your phone terminal. So lets see how you can install it...
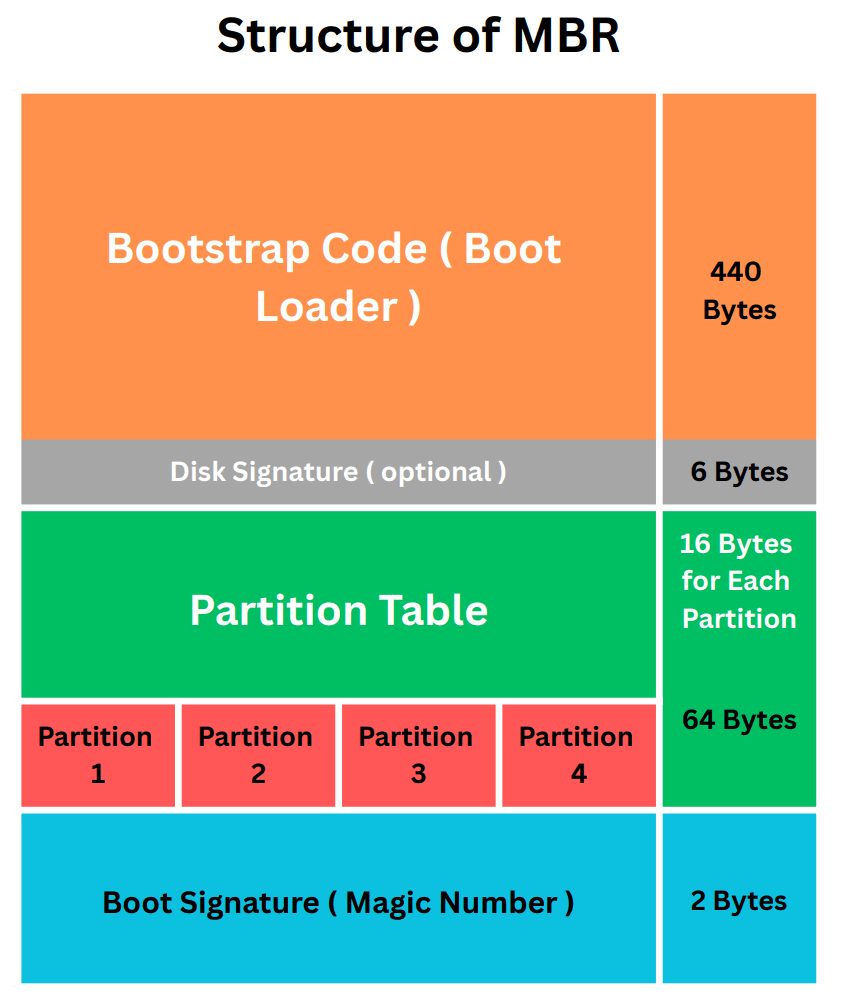
GPT or GUID Partition Table is a successor of MBR that comes with a lot of amazing features to protect your data's integrity security and safety...
Congratulations! If you are reading this, you have likely finished setting up your cyber security home lab....
In this part, we are going to install WSL and Docker on our machine. If you don't have a high-configuration computer at your hands,...
In this blog, I'm going to show you how you can create your first virtual machine with VMware. At first, the virtualization concept and the thought of creating your first...
Wanted to share my personal update, so here I am with another self blog. It's been 6 months since I wrote an update about my journey,...
This is my first blog of my journey which I am sharing with you.So, till this point, I have started a YouTube channel named Growing HackerAs you can see above...