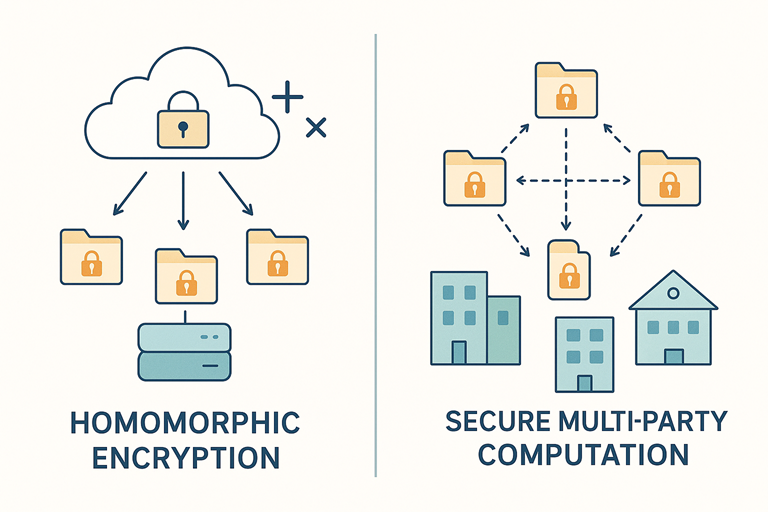
In our previous discussion on Key Exchange and Key Management in Cryptography, we explored how two parties can agree on a secret key without exposing it to eavesdroppers. Today, let’s journey into a more futuristic concept: performing computations on encrypted data itself. Sounds like magic, right? Yet, thanks to Homomorphic Encryption (HE) and Secure Multi-Party Computation (SMPC), this is no longer a sci-fi dream but a budding reality. Given the rapidly evolving landscape—new research breakthroughs, growing enterprise adoption, and hardware accelerators—understanding these techniques is more important than ever for anyone interested in cryptography, online security, or cyber security.
Why Compute on Encrypted Data?
Imagine you’re collaborating with several hospitals on medical research. Each institution has sensitive patient records that cannot be shared directly due to privacy laws. You still want to calculate, say, the average recovery time for a particular treatment across all datasets. Traditionally, you’d have to share raw data (or anonymized—but often reversible—datasets), send it to a trusted third party, or find some other workaround. With HE and SMPC, however, you can compute that average without ever revealing individual patient records. The data stays encrypted throughout the entire process—no peeking, no leaks.
This notion seems almost counterintuitive: how can one perform any meaningful operation—addition, multiplication, even machine learning inference—on ciphertext? That’s exactly what homomorphic encryption enables, and SMPC generalises this idea for collaborative scenarios. But as promising as they sound, both come with their own sets of challenges and trade-offs. Let’s dive in.
Homomorphic Encryption: Doing Maths on Ciphertext
Homomorphic Encryption (HE) is a cryptographic technique that lets you perform arithmetic operations on ciphertexts. When you decrypt the result, you get exactly what you’d have obtained if you’d operated on the plaintext directly. In other words:
Traditional: Plaintext → Encrypt → Decrypt → Compute → Encrypt
Homomorphic: Plaintext → Encrypt → Compute → Decrypt
This leap is a game-changer for cloud computing. You can upload encrypted data to a cloud service, let the cloud provider run computations, and retrieve only the encrypted output—never revealing your sensitive inputs to the provider.
Recent Breakthroughs
- Large-Integer Homomorphic Schemes: In early 2025, Dan Boneh and Jaehyung Kim from Stanford introduced a new FHE system tailored for arithmetic over large primes (256-bit and even 2048-bit) by composing nested residue number systems. Their implementation outperforms previous TFHE-rs libraries by roughly 1,000× in multiplication throughput for 256-bit integers and yields a 10× latency improvement. For 2048-bit moduli, performance leaps are even larger. (Cryptology ePrint Archive)
- Hardware Accelerators: At DATE 2025, researchers from TU Graz and Universidad Politécnica de Madrid unveiled PASTA—an FPGA/ASIC accelerator for Hybrid Homomorphic Encryption (HHE). Compared to a CPU, PASTA achieves up to a 171× speedup for encryption tasks on low-end 130 nm ASICs and a 97× boost on 7 nm/28 nm platforms over previous public-key accelerators. These hardware advancements are crucial to narrowing the performance gap for real-time applications. (date25.date-conference.com)
- Open-Source Toolkits: Google continues expanding its FHE toolkit, now supporting video processing, private machine learning, and text analysis on encrypted data—embracing both software libraries and dedicated hardware modules to lower barriers to adoption. (Google Developers Blog)
Market and Adoption Trends
- Enterprise Uptake: According to a 2025 market analysis, 73% of cloud service providers are integrating HE into their security stacks—a 47% jump from the previous year. Industries like finance and healthcare are leading the charge, with 77% of financial institutions and 72% of hospitals adopting HE for compliant, privacy-preserving analytics. (Global Growth Insights, openPR.com)
- Geographical Insights: Europe holds a 61% share in HE adoption (driven by GDPR mandates), whereas Asia-Pacific adoption has jumped to 57%, thanks to rising cybersecurity concerns and cloud migrations in China, Japan, and India. (Global Growth Insights)
Challenges Remain
Of course, the hype comes with caveats. HE’s computational overhead remains a major bottleneck—processing times can be 5× slower than with plaintext, and real-time applications see delays up to 58%. Many enterprises report a 62% increase in infrastructure costs to support HE’s processing demands. Furthermore, scalability and integration complexity are hurdles, as 59% of organisations struggle with deployment and 66% cite expertise gaps. (Global Growth Insights, Medium)
Secure Multi-Party Computation: Privacy in Collaboration
Secure Multi-Party Computation (SMPC) extends cryptographic ideas so that multiple parties can compute a joint function over their inputs without ever revealing those inputs to each other. At the end, everyone only learns the agreed-upon output, never the individual secrets.
Real-World Use Cases
- Healthcare Research: Multiple hospitals pool genomic data to train a machine-learning model for disease prediction. No hospital ever sees another’s raw DNA sequences; rather, they engage in an SMPC protocol, learn model weights or aggregated statistics, and collaborate securely. (AllCyberSecurityMagazine)
- Finance: Banks analyse collective credit risk or perform private auctions without exposing customer data. SMPC lets them calculate joint risk metrics or auction winners without revealing individual bids or balances. (MarketsandMarkets)
Market Dynamics
- Rapid Growth: The global SMPC market reached USD 1.03 billion in 2024 and is projected to hit USD 1.13 billion in 2025, with a CAGR of ~10%, reaching USD 1.82 billion by 2030. (360iResearch, The Business Research Company)
- Sector Adoption:
- Finance & Insurance: estimated 62% of fintech companies now incorporate SMPC protocols for fraud detection, risk analysis, and regulatory compliance.
- Healthcare: more than 73% of biotech firms use SMPC for secure multi-institutional clinical trials and shared analytics. (MarketsandMarkets, AllCyberSecurityMagazine)
Recent Innovations
- Open Sourcing at Scale: In mid-2024, Worldcoin, co-founded by Sam Altman, released its SMPC system for biometric deduplication (iris code matching) under an open-source license. This system is designed to be quantum-resistant and scalable, solving problems around cryptographic scale and resource constraints. (Biometric Update)
- Cloud Integration: Major cloud providers are embedding SMPC modules directly into their platforms, allowing developers to spin up “privacy-guarded” computation instances seamlessly. The integration of SMPC with serverless architectures is particularly promising, ensuring computations remain private even when using microservices. (MarketsandMarkets)
Challenges Ahead
However, SMPC isn’t a silver bullet. Protocols often involve heavy communication overhead—multiple rounds of ciphertext exchanges can choke bandwidth, especially when parties are geo-dispersed. Scalability is painful too: handling large datasets or dozens of parties can balloon both computation and communication costs. Moreover, the field lacks a fully standardized toolkit, so interoperability between different SMPC frameworks remains a headache. (United States Cybersecurity Magazine, MarketsandMarkets)
Connecting the Dots: HE, SMPC, and What’s Next
Given their complementary strengths, it’s natural to ask: can we blend HE and SMPC for even stronger privacy guarantees? Indeed, Hybrid HE/SMPC approaches have emerged, where each party applies lightweight symmetric encryption (from HHE schemes like PASTA) on the client end and delegates heavy homomorphic decryption to a server or consortium. This reduces the computational burden on individual participants while retaining strong privacy properties. (date25.date-conference.com)
Looking forward, our next instalment will explore Cryptography in Blockchain and Cryptocurrencies. Both HE and SMPC have begun seeping into blockchain ecosystems—private smart contracts on Layer 2 networks may leverage SMPC for confidential DeFi auctions, while homomorphic techniques can enable privacy-preserving staking analytics. Stay tuned!
Nuances, Trade-offs, and Practical Tips
- Latency vs. Privacy
- If you need real-time analytics (e.g., fraud detection in high-frequency trading), pure FHE might be too slow. Consider HHE (symmetrically encrypted front-end) or SMPC with fewer rounds.
- For batch data processing (e.g., large-scale genomic studies), FHE’s overhead is more tolerable—especially with new implementations supporting 256-bit primes or more. (Cryptology ePrint Archive, date25.date-conference.com)
- Infrastructure and Costs
- Hardware Accelerators: If your organisation can invest in dedicated FPGA/ASIC modules (e.g., PASTA), you’ll see significant speedups. Otherwise, cloud-based “FHE instances” from major providers are becoming available—albeit at a premium cost. (Google Developers Blog, date25.date-conference.com)
- Cloud vs. On-Prem: Cloud integration of SMPC/HE is booming. However, if you’re in a tightly regulated environment (like certain government agencies), on-premise solutions with local accelerators might be preferable.
- Ecosystem Maturity
- Software Toolkits: Libraries such as Microsoft SEAL, Google’s open-source FHE transpiler, and open-sourced SMPC frameworks (like Worldcoin’s) are continually evolving.
- Community and Support: Unlike more “mature” crypto (RSA, AES), HE/SMPC still have a steep learning curve. You’ll need cryptographic expertise on your team—or partner with specialists.
- Regulatory Compliance
- In regions governed by GDPR, CCPA, or emerging Indian data-protection laws, HE and SMPC can help you process user data without direct exposure, which eases compliance.
- Financial regulators (e.g., RBI in India) are exploring encrypted analytics for risk assessments—watch this space for region-specific guidelines.
FAQs
Q: Is Homomorphic Encryption practical for everyday use?
A: For most consumers, yet no. It’s still better suited for organisations with stringent privacy needs and budgets for high-performance hardware or cloud credits. But thanks to advances—FHE transcoders, hardware accelerators, and new schemes—real-world deployments are accelerating (e.g., fraud analytics in fintech, genomics in biotech). (Global Growth Insights, Cryptology ePrint Archive, Google Developers Blog)
Q: How is SMPC different from HE, and which should I pick?
A: HE focuses on single-party encrypted computations (you hold all ciphertexts), while SMPC lets multiple parties jointly compute without pooling their data. If you need to collaborate with external entities, SMPC is your friend; if you simply want to outsource encrypted data analysis to the cloud, HE is more appropriate. Hybrid schemes combine both for nuanced use cases. (United States Cybersecurity Magazine, date25.date-conference.com)
Q: Will quantum computers break HE, SMPC schemes?
A: Post-quantum cryptography is an area of active research. Many HE and SMPC protocols rely on lattice-based hardness assumptions believed to be quantum-resistant. However, adopting post-quantum variants is advisable if you expect data to be sensitive decades into the future. (United States Cybersecurity Magazine, MarketsandMarkets)
Q: How do HE and SMPC trends affect online security and cyber security?
A: Both HE and SMPC elevate data privacy by ensuring sensitive information never appears in plaintext during processing. This reduces attack surfaces, limits insider threats, and makes large-scale data breaches significantly harder. (Global Growth Insights, MarketsandMarkets, 360iResearch)
Q: What is Secure Multi-Party Computation?
A: SMPC lets multiple parties compute a result together without revealing their private data. Everyone keeps their inputs secret, but still gets the correct shared output.
Q: What’s an example of Multi-Party Computation?
A: Banks can use SMPC to detect fraud together without sharing sensitive customer data. It’s like solving a puzzle without showing anyone your piece.
Q: What is Secure Multi-Party Computation on Blockchain?
A: SMPC on blockchain allows private computations in a decentralized setup. It adds privacy to blockchain’s transparency—useful for voting, auctions, or private DeFi analytics.
Q: What do you mean by Homomorphic Encryption?
A: Homomorphic Encryption (HE) lets you perform calculations on encrypted data—without ever needing to decrypt it. Once you decrypt the final result, it’s as if the operations were done on the original plain data.
Q: What is a practical example of Homomorphic Encryption?
A: Suppose a hospital encrypts patient data and sends it to a cloud service for analysis. With HE, the cloud can compute stats or predictions on that encrypted data—without ever seeing the actual medical records.
Q: Is RSA a Homomorphic Encryption?
A: Yes, but only partially. RSA supports multiplicative homomorphism—you can multiply two encrypted numbers and get the right result after decryption. But it’s not fully homomorphic like modern HE schemes (e.g., BFV, CKKS).