Over 900k users were hit by malicious Chrome extensions posing as ChatGPT and DeepSeek tools. We dive deep into the analysis, the C2 exfiltration, and how to secure your browser....

Understanding Cyber Threats and Vulnerabilities
Cyber Threats are increasing and criminals to so why not learn about some cool tools and techniques used by hackers?

Salt, Pepper, and Hashing: Three Ingredients to Secure Passwords
Our password travel on a boat in an open ocean that everyone has access to. We will see how Hashing, peppering and salting actually save us from hackers on the internet..

Creating and Breaking MD5 Hash
We will see how MD5 is created and why it is not considered secure anymore. How Hackers have managed to Hack the Hashes

EFI Partition: What it is and Why it’s Important
EFI or Extensible Firmware Interface is a firmware interface that is used to boot operating systems in computers. Let's see what's inside?

What is ADB and How To Install it in Windows and Linux ?
adb stands for Android Debug Bridge by which you can get root access to your phone terminal. So lets see how you can install it
How To Type Hindi Using English in Windows 11
Learn how to type in Hindi without the need for any third-party software on Windows. In this Article I will teach you how you can type English to Hindi effortlessly in Windows

I Changed My Whole Life in 6 Months
Wanted to share my personal update, so here I am with another self blog. It's been 6 months since I wrote an update about my journey,

Fundamentals of Cyber Security for Beginners
Being secure is crucial in this world specially online one single mistake can lead to bankruptcy let's look how you can protect yourself online.
How do Computers Boot? | Booting Process Explained
Have you ever wondered what happens when you click the power button of you PC How does it boot on How the OS loads. We will explore how your computer starts.
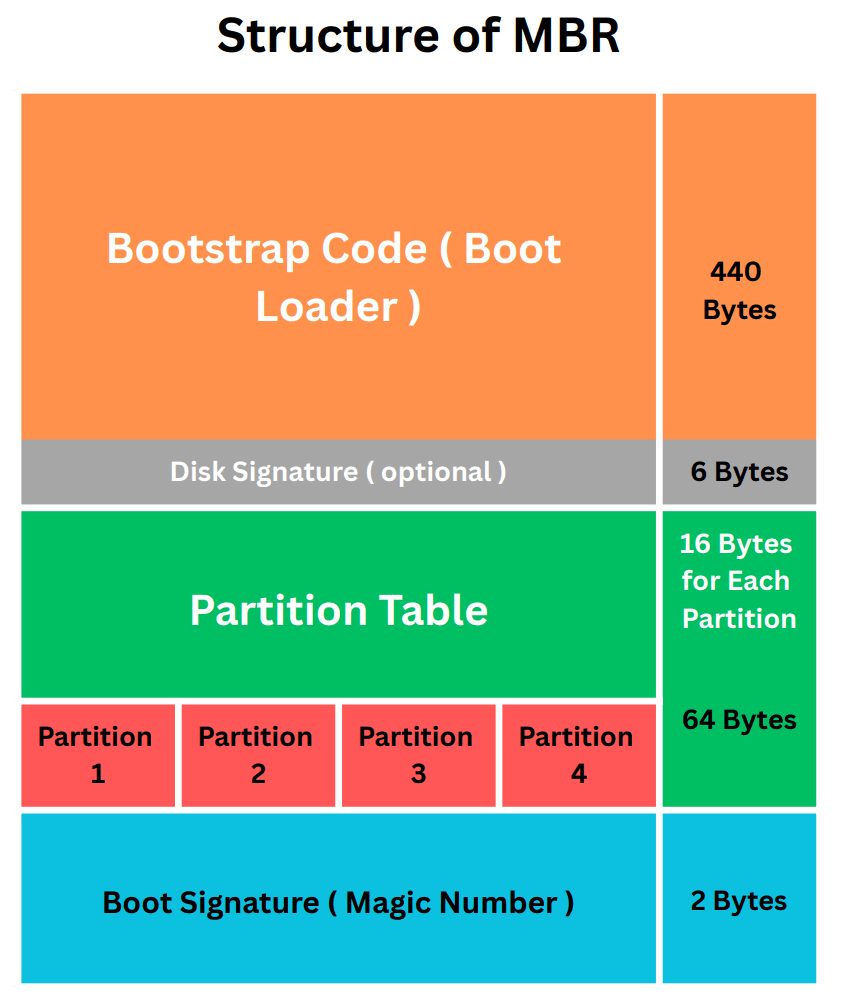
What is MBR, it’s Working and Hacking !!
MBR or Master Boot Record is a partition scheme that has been used for decades. In this blog we will see MBR structure, history and hacking possibilities.
