Over 900k users were hit by malicious Chrome extensions posing as ChatGPT and DeepSeek tools. We dive deep into the analysis, the C2 exfiltration, and how to secure your browser....

A Simple Intro To Linux Process and Services Management
Master Process and Services Management in Linux! Learn to hunt malicious daemons, juggle background tasks, and keep your hacker system running smoothly.
How to Create Linux Service ? A Complete Guide
Learn how to create linux service files, manage background processes, and troubleshoot systemd units.

How Packages Work in Linux ? Everything You Need To Know !!
Packages power everything inside your OS — but what are they, how do they work, and how do you install them? Let’s break it down in a way that finally makes it all click.

You Need To Know Group Management In Linux !
Group Management in Linux is crucial for cybersecurity, as poorly configured groups can easily become a hacker’s best friend. That’s why it’s important to learn about group management as soon as possible!

What’s Next? Leveraging Your Cyber Security Home Lab for Mastery
Congratulations! If you are reading this, you have likely finished setting up your cyber security home lab.

How Malicious Chrome Extensions Exposed 900K Users This December ?
Over 900k users were hit by malicious Chrome extensions posing as ChatGPT and DeepSeek tools. We dive deep into the analysis, the C2 exfiltration, and how to secure your browser.

User Management in Linux: Everything You Need to Know ?
User Management in Linux is a crucial concept to master for maintaining security. In this article we are going to learn everything necessary for managing users in Linux.

What is WinGet? The Magic of Windows Package Manager
Winget is just like magic for Windows. It is a Package Manager for Windows, which can be used to install multiple software just by a simple command.

How WinGet Works ? The Magic of CDN in Package Manger
The working of Winget is a little more complex than you think. In this blog I will show you how CDN help Winget to speed up and fulfill your needs.
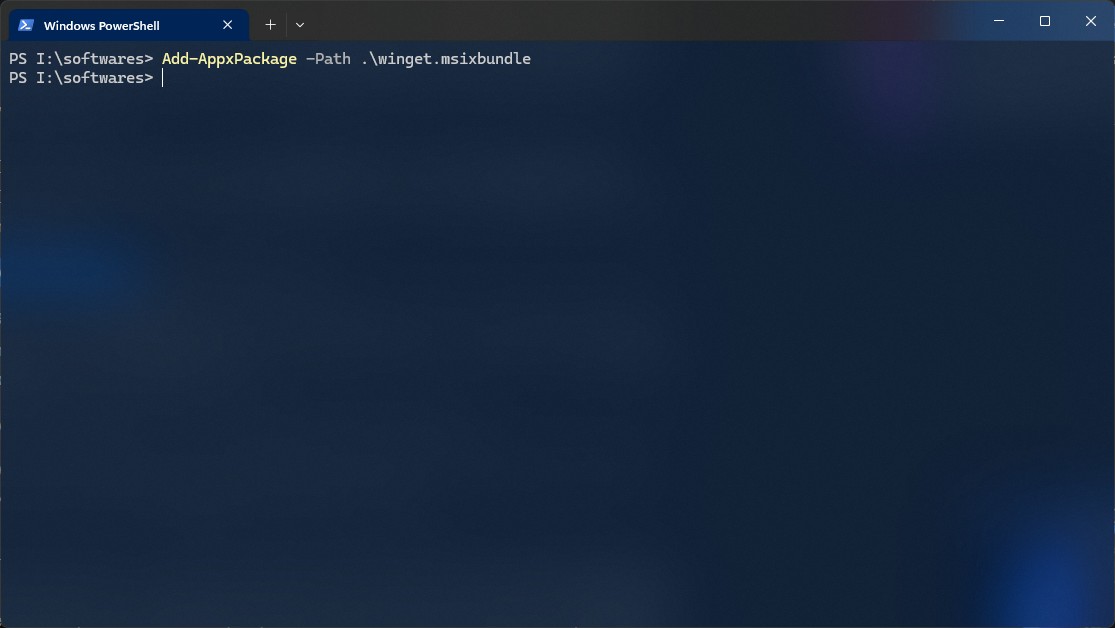
How to Download and Install WinGet on Windows 10 & 11?
Winget is a package manager for your Windows machine. But what if you don't have Winget installed on your Windows machine? Well, in this blog, I'm going to show you how you can download and install Winget for your Windows machine.
