Over 900k users were hit by malicious Chrome extensions posing as ChatGPT and DeepSeek tools. We dive deep into the analysis, the C2 exfiltration, and how to secure your browser....

How Malicious Chrome Extensions Exposed 900K Users This December ?
Over 900k users were hit by malicious Chrome extensions posing as ChatGPT and DeepSeek tools. We dive deep into the analysis, the C2 exfiltration, and how to secure your browser.

How WinGet Works ? The Magic of CDN in Package Manger
The working of Winget is a little more complex than you think. In this blog I will show you how CDN help Winget to speed up and fulfill your needs.

Cryptography for Network Security and Secure Communication
Cryptography underpins secure communication and network security—protecting your data in transit, beating cyber threats, and shaping a safer online world.
Quantum Cryptography & Post‑Quantum Cryptography: The New Era !
Dive into Quantum Cryptography and Post‑Quantum Cryptography with real-world analogies, expert insights, and engaging storytelling for tech‑savvy minds passionate about cyber security.

Cryptography in Blockchain and Cryptocurrencies: And it’s Future !
Cryptography in blockchain underpins online security and cyber security—from hashing and digital signatures to the looming quantum threat.
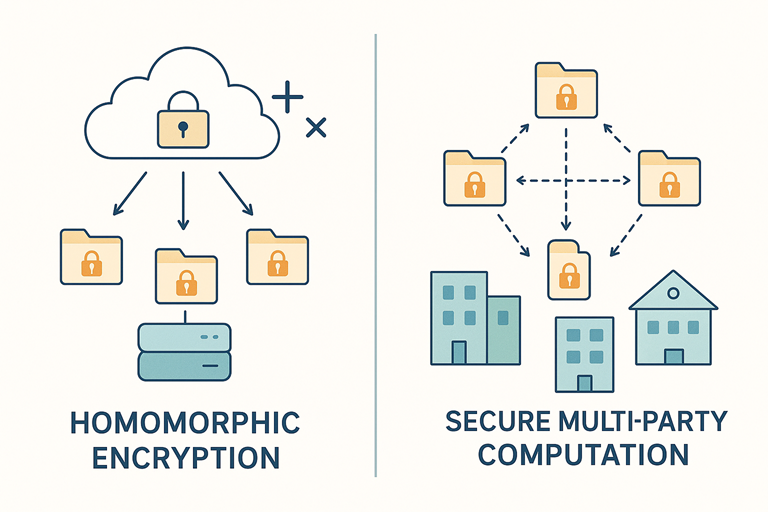
SMPC & Homomorphic Encryption: No Need to Decrypt
Explore the latest in Homomorphic Encryption and Secure Multi-Party Computation—including 2025 research breakthroughs, market growth, and real-world applications—to see how encrypted data processing boosts online security and cyber security.
Key Exchange and Management in Cryptography: Keeping Secrets Safe
Discover how key exchange and key management work in cryptography—from Diffie-Hellman to modern TLS. Learn best practices to keep your data secure! 🔐

You must Know About Cryptanalysis and Cryptographic Attacks Now!
Dive into the world of cryptanalysis and discover how understanding cryptographic attacks enhances online security and fortifies cyber defenses.
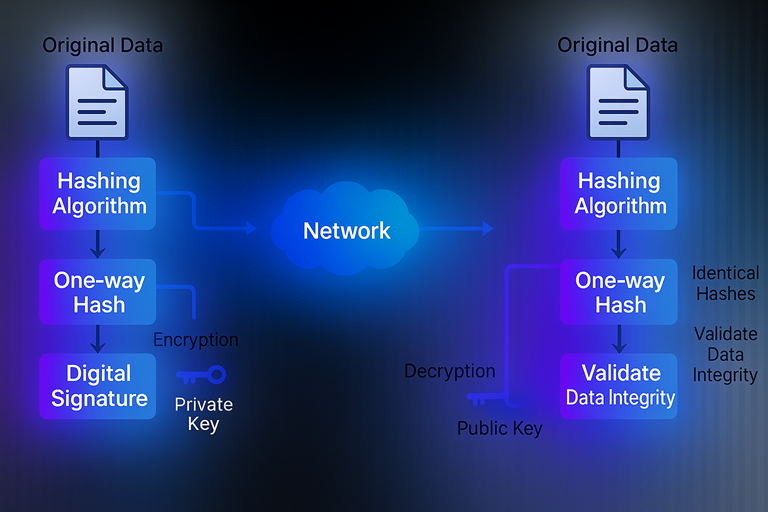
What are Cryptographic Hash Functions and Digital Signatures ?
Explore how cryptographic hash functions and digital signatures work together to ensure online security, data integrity, and trust in the digital world.

Cryptography for Data Integrity and Authentication
modern cryptography isn’t only about hiding secrets. It’s just as much about proving that a file, message, or software update really came from the right person and hasn’t been silently tweaked along the way.
