Over 900k users were hit by malicious Chrome extensions posing as ChatGPT and DeepSeek tools. We dive deep into the analysis, the C2 exfiltration, and how to secure your browser....

How to Install Wazuh on Raspberry Pi ?
Let's, Install Wazuh server on a raspberry Pi. In this blog, I will give you a step-by-step installation process of Wazuh server on raspberry pi.

How to Fix the Blinking Orange Light on a MI Xiaomi Camera 360
Recently, my Xiaomi Camera 360 (Model No: MJSXJ05CM) stopped working. So, I did what any sane person would do: I tried resetting the camera. It spun 360 degrees and stopped at the Mi logo. I thought, "Yes, problem solved! 😂" But no such luck. The camera's LED just kept blinking orange non-stop.

Information Gathering in Linux | Part 3
Dive into Information Gathering in Linux with System Information Part-3. Learn to explore devices, processes, and more with lsblk, lsusb, lspci, and lsof.

Information Gathering in Linux | Part 2
Take your Linux information gathering skills to the next level! Learn to use ss, ps, who, and w to uncover running processes, active users, and network connections. Essential for any hacker.

Information Gathering in Linux | Part 1
Learn how to gather system-level details in Linux using commands like whoami, id, hostname, uname, ifconfig, ip, and netstat. Ideal for beginners in ethical hacking!

Learn Find Now : The Boss of Searching in Linux !!
Learn how to master the find command in Linux with advanced flags like -user, -exec, and how to pair it with the file command. Perfect for ethical hackers in Hindi.

Cryptography for Network Security and Secure Communication
Cryptography underpins secure communication and network security—protecting your data in transit, beating cyber threats, and shaping a safer online world.
Quantum Cryptography & Post‑Quantum Cryptography: The New Era !
Dive into Quantum Cryptography and Post‑Quantum Cryptography with real-world analogies, expert insights, and engaging storytelling for tech‑savvy minds passionate about cyber security.

Cryptography in Blockchain and Cryptocurrencies: And it’s Future !
Cryptography in blockchain underpins online security and cyber security—from hashing and digital signatures to the looming quantum threat.
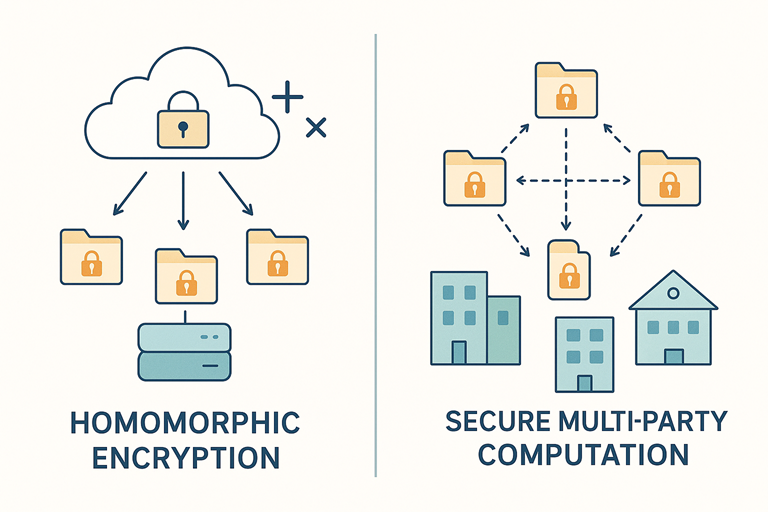
SMPC & Homomorphic Encryption: No Need to Decrypt
Explore the latest in Homomorphic Encryption and Secure Multi-Party Computation—including 2025 research breakthroughs, market growth, and real-world applications—to see how encrypted data processing boosts online security and cyber security.
