Before we dive in, here’s the quick takeaway: modern cryptography isn’t only about hiding secrets. It’s just as much about proving that a file, message, or software update really came from the right person and hasn’t been silently tweaked along the way. We’ll chat about why that matters to everyday online security, explore the deceptively simple-looking building blocks (MACs, HMAC, AES-GCM), and peek at real-world stories—from Git commits to WhatsApp safety numbers—that show these ideas in action. Ready? Grab a cup of coffee (or chai, no judgement 🙂) and let’s roll.
- Why “untouched” data matters
- Integrity Vs Authentication
- 🔍 Understanding Data Integrity in Cryptography
- 🛡️ The Role of Authentication in Cryptography
- Meet the workhorse: The Message Authentication Code (MAC)
- Authenticated Encryption: no more two-padlocks
- Integrity in the wild
- Common cracks in the armour
- Best-practice cheat sheet
- Looking ahead
Why “untouched” data matters
In the security triad of confidentiality, integrity, and availability, integrity is the quiet middle child ignored until something goes wrong. Integrity means the information you receive is exactly what the sender produced, no silent flips, swaps, or malicious additions. NIST defines it crisply as “data that has not been altered in an unauthorized manner.” (NIST CSRC)
Think about a software-update package. If an attacker can inject just a few malicious bytes, your laptop might happily run ransomware —even if the update was downloaded over an encrypted tunnel. Scary, right? That’s why integrity always travels in tandem with confidentiality in serious cyber security designs. (tutorialspoint.com)
Integrity Vs Authentication
Integrity answers “Did the content change?” Authentication answers “Did the right person send it?”. Together, they guarantee trust. Many cryptographic tools bundle both promises, because knowing a file is untouched is pointless if you aren’t sure whose file it is in the first place—and vice-versa. (Fortinet)
Absolutely! Let’s enrich the article by adding two dedicated sections that delve deeper into Data Integrity and Authentication in the context of cryptography. These additions will provide a clearer understanding of these fundamental concepts and their real-world applications.
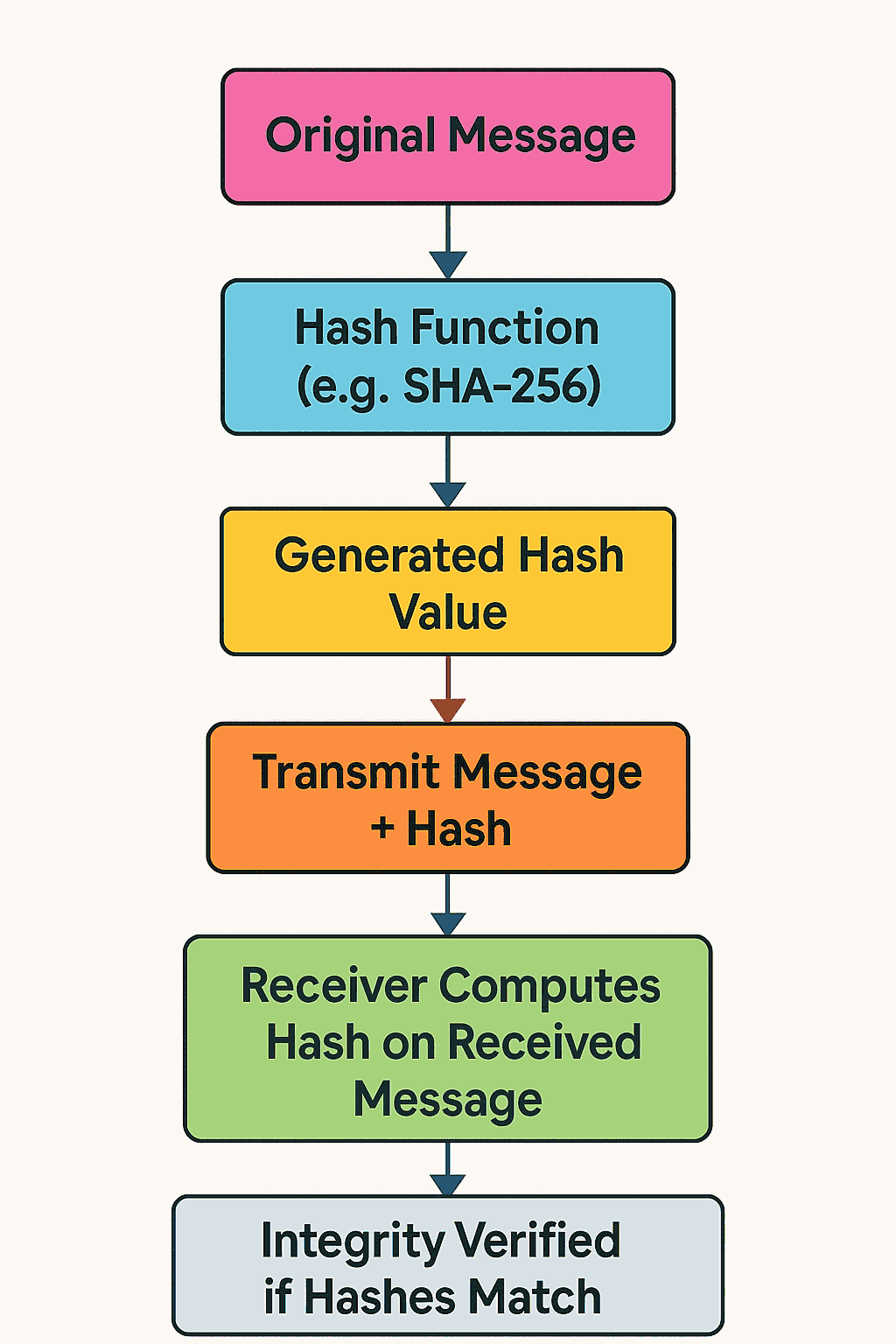
🔍 Understanding Data Integrity in Cryptography
Imagine you’re sending a heartfelt letter to a friend. You want to ensure that the message arrives exactly as you wrote it, without any alterations. In the digital realm, this assurance is what we refer to as data integrity.
What Is Data Integrity?
At its core, data integrity ensures that information remains accurate and unaltered during storage or transmission. It’s about guaranteeing that the data received is precisely what was sent, free from tampering or corruption.
How Cryptography Ensures Integrity
Cryptography employs several mechanisms to uphold data integrity:
- Hash Functions: These are mathematical algorithms that convert data into a fixed-size string of characters, which appears random. Any change in the original data, no matter how minor, results in a completely different hash value. This property makes hash functions ideal for verifying data integrity.
- Message Authentication Codes (MACs): A MAC is a short piece of information used to authenticate a message and to provide integrity and authenticity assurances. It involves a secret key shared between the sender and receiver, ensuring that any alteration in the message can be detected.
- Digital Signatures: These are cryptographic techniques that not only verify the authenticity of a message but also ensure its integrity. A digital signature is created using the sender’s private key and can be verified by anyone with access to the corresponding public key.
Real-World Applications
- Software Updates: When you download software updates, cryptographic hashes are often used to verify that the files haven’t been tampered with during transmission.
- Financial Transactions: Banks use cryptographic techniques to ensure that transaction data remains unaltered, maintaining trust in digital banking systems.
- Healthcare Records: Ensuring the integrity of electronic health records is crucial for patient safety and confidentiality.
🛡️ The Role of Authentication in Cryptography
Now, let’s consider another scenario: receiving a message that appears to be from your bank, asking for sensitive information. How can you be certain it’s genuinely from your bank and not a malicious actor? This is where authentication comes into play.
What Is Authentication?
Authentication in cryptography is the process of verifying the identity of a user or system. It’s about ensuring that the entity you’re communicating with is indeed who they claim to be.
Cryptographic Techniques for Authentication
- Digital Signatures: As mentioned earlier, digital signatures not only ensure data integrity but also authenticate the sender’s identity. Since only the sender possesses the private key used to create the signature, its validity confirms the sender’s authenticity.
- Public Key Infrastructure (PKI): PKI is a framework that uses a pair of keys (public and private) and digital certificates to authenticate users and devices. It’s widely used in securing web communications through HTTPS.
- Challenge-Response Protocols: These involve one party presenting a question (“challenge”) and the other providing a valid answer (“response”) to verify identity. It’s commonly used in systems requiring two-factor authentication.
Everyday Examples
- Secure Websites (HTTPS): When you visit a secure website, your browser uses certificates to authenticate the site’s identity, ensuring you’re not communicating with an imposter.
- Email Security: Email services use authentication protocols like SPF, DKIM, and DMARC to verify that incoming messages are from legitimate sources.
- Access Control Systems: From swiping a card to using biometric data, authentication ensures that only authorized individuals can access certain areas or information.
Meet the workhorse: The Message Authentication Code (MAC)
A Message Authentication Code (MAC) is like a wax seal on an old-school letter. The sender and receiver share a secret key; the sender stamps a short tag over the message, and the receiver re-stamps to see whether the tags match. If they do, the message is genuine and unaltered. Simple in concept, but devilishly subtle in the maths. (Fortinet)
HMAC—adding hash power
The most popular MAC on the internet today is HMAC (Hash-based MAC). Picture it as wrapping a regular cryptographic hash (say, SHA-256) inside two layers of key-flavoured padding—like a masala dosa with chutney on both sides. If any single bit of the message flips, the final tag changes unpredictably. HMAC has held up to decades of public scrutiny and is what protects your bank’s API calls and many JWT tokens. (Medium)
Block-cipher MACs (CBC-MAC, CMAC…)
Not all MACs rely on hashes; some use block ciphers under the hood. CBC-MAC, for instance, chains blocks together to brew a tag. But—small rant incoming—CBC-MAC is only safe for fixed-length messages. Attackers can glue extra blocks and forge valid tags if you aren’t careful (academics call these “multiple forgery attacks”). (NIST CSRC) Most practitioners now prefer CMAC or GMAC, which plug those design holes.
Authenticated Encryption: no more two-padlocks
Carrying both encryption and a separate MAC can feel like travelling with two heavy padlocks. Authenticated Encryption with Associated Data (AEAD) modes—like AES-GCM—combine the two jobs into one slick algorithm. Encrypt, attach a tag, done. That’s why modern protocols (TLS 1.3, WireGuard, QUIC) lean heavily on AEAD. (Cryptography Stack Exchange)
Integrity in the wild
TLS records
Every time you hit a URL that starts with https:// TLS chops your data into “records”. Each record is encrypted and bundled with a MAC (or AEAD tag) before it leaves your device, so an on-path attacker can’t flip even a single byte without getting caught. (Wikipedia)
Git commit hashes
If you’re a developer, git status is practically muscle memory. Behind the scenes, Git stuffs every commit, tree, and blob into a SHA-1/SHA-256 hash. When you pull from a remote, Git recomputes those hashes to ensure the project history wasn’t forged in transit. Integrity isn’t an optional extra; it’s baked into the design.
WhatsApp “safety” numbers
Ever noticed a long 60-digit code when you open “Encryption” info in a WhatsApp chat? That’s effectively a human-readable fingerprint of the chat’s shared secret key. When your friend scans or reads back the same code, both of you confirm authenticity—and any man-in-the-middle skulking on the Wi-Fi would fail the test.
National-scale stakes: Aadhaar
India’s UIDAI doesn’t gamble with billions of residents’ biometric data. Fingerprint templates are encrypted on the sensor itself, zipped through a PKI tunnel, and verified only inside UIDAI’s secure vaults, ensuring authenticity and freshness at each hop. (UIDAI)
Common cracks in the armour
- Hash collisions – When Google’s researchers shattered SHA-1 a few years back, they proved that two entirely different PDFs could share the same hash. If your integrity check relies on SHA-1 alone, an attacker might sneak in a malicious twin. Time to upgrade to SHA-256 or SHA-3.
- Supply-chain blind spots – OWASP lists “Software and Data Integrity Failures” as a Top-10 risk. Grabbing third-party libraries over insecure channels or skipping signature checks in your CI/CD pipeline gives attackers a Trojan horse as a gift.
- Weak MAC usage – Using CBC-MAC for variable-length messages? You could be offering a buffet to forgery attacks. Stick with vetted constructions like HMAC or GMAC.
- Broken trust anchors – If the Certificate Authority signing your TLS certificate is compromised, authentication falls apart. Good PKI hygiene (certificate transparency logs, short-lived certs) is non-negotiable.
Best-practice cheat sheet
- Use AEAD by default – AES-GCM, ChaCha20-Poly1305, or equivalent.
- Pick modern hashes – SHA-256/SHA-3; retire MD5 and SHA-1.
- Rotate keys – Long-lived keys are sitting ducks.
- Layer in PKI – Signed certificates bind identities to keys.
- Automate checks in CI/CD pipelines – Verify signatures on every dependency pull.
- Log and monitor – Sudden MAC failures or certificate changes may signal tampering.
(Quick anecdote: I once spent two caffeine-fuelled days debugging “random” API failures—turned out the HMAC secret in staging had drifted one character. Monitoring would have saved a lot of midnight oil.)
Looking ahead
In the next part of our Cryptography for Everyone series, we’ll zoom in on cryptographic hash functions and digital signatures—the dynamic duo that underpin everything from Bitcoin to Aadhaar e-sign. Until then, stay curious and keep those keys secret. 😊
Meta description
Learn how cryptography preserves data integrity and authenticates messages using MACs, HMAC, AES-GCM, and real-world examples like TLS, Git, and WhatsApp.
FAQs
Q1. Is encryption alone enough for online security?
No. Encryption hides data, but attackers can still tamper with ciphertext. You need integrity checks (MACs or AEAD) to detect modifications. (Wikipedia)
Q2. What’s the difference between HMAC-SHA-256 and plain SHA-256?
Plain SHA-256 is a hash; anyone can recompute it. HMAC-SHA-256 mixes in a secret key, so only someone with that key can produce or verify the tag, providing both integrity and authentication. (Medium)
Q3. How often should I rotate MAC or encryption keys?
There’s no one-size-fits-all number, but most organisations rotate symmetric keys every few months—and immediately after any suspected compromise—to limit the blast radius. (OWASP Foundation)
Q4. Are digital signatures different from MACs?
Yes. MACs require the sender and receiver to share the same secret key, whereas digital signatures rely on asymmetric cryptography—anyone can verify with the public key, but only the signer knows the private key. We’ll cover that in depth next time. (Identification for Development)