The world of hacking and cyber security wants you to learn Linux while there are multiple Linux distros out there, Kali Linux is the best for penetration testing and security auditing.
But you know all this right? So, let’s see how you can install Kali Linux on your PC. There are multiple ways to install Kali Linux on a Computer, but not all of them are easy, especially for a beginner who is still exploring different stuff!!
I have installed Kali Linux multiple times on multiple devices and can say that the best way to install Kali Linux on a device is to use a Virtual Machine.
Why use Virtual Machines?
You can dual boot Kali Linux with another operating system or just install Kali Linux on a device but there are some problems with this approach. Using just Kali Linux as your Operating System makes it difficult to perform day-to-day tasks like using Word, Excel Gaming, etc. and as a beginner who is just starting, you might not have another computer on which you can use Kali Linux. ( I didn’t? at least) I myself use VMware, but you can use any virtual machine software of your choice.
If you are not sure what virtual machine to use, don’t worry read the article below to get a better comparison between the top virtual machines that you can use.
Top 4 Best Virtual Machines For Hacking
System Requirements
It’s important to know the software’s minimum system requirements before installing Virtual Machines since they are not lightweight software to run on a PC and take some actual power. ( Don’t worry it’s not even that demanding ?)
Hardware Requirements
- A computer with at least a 2 GHz dual-core processor or higher
- A minimum of 2 GB RAM (recommended: 4 GB or more) for smooth performance
- At least 20 GB of free hard disk space for Kali Linux installation ( I have written 20GB, but you should have 40 to 50GB free space ?)
- A network adapter for network connectivity in the virtual machine
Software Requirements
Any one of the 3 Virtual machine software
- VMware
- VirtualBox
- QEMU
I suggest you use VMware since it’s more beginner-friendly and easy to use.
Step-by-Step Installation Guide for Kali Linux on VirtualBox
❗❗ You will have to download any of the three VM software mentioned above first before moving to other steps ❗❗
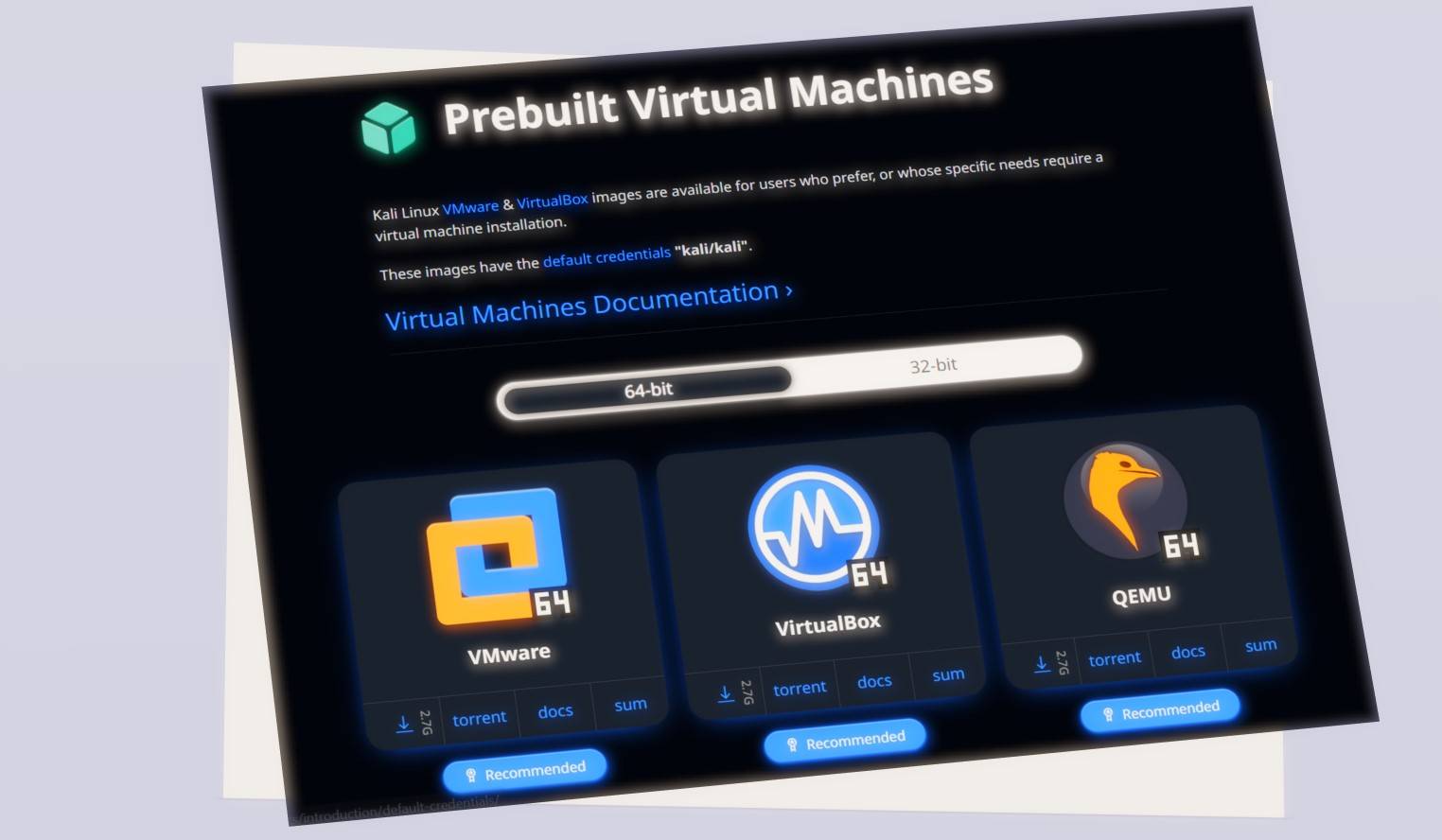
1) Download Kali Linux Virtual Machine
Head on to the Kali Linux download page link: Get Kali. Under Prebuild Virtual Machines Section download your desired prebuild VM ( I am downloading VMware here ? )

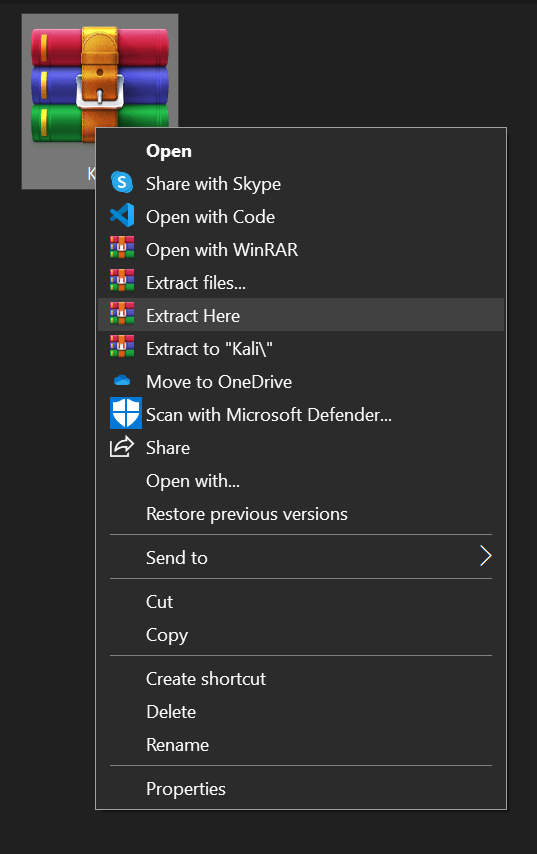
2) Extract the Downloaded File
After the download is complete open the folder where you installed the Kali Linux file and extract it. Here I have used WinRAR you can also use 7zip or any other software you like
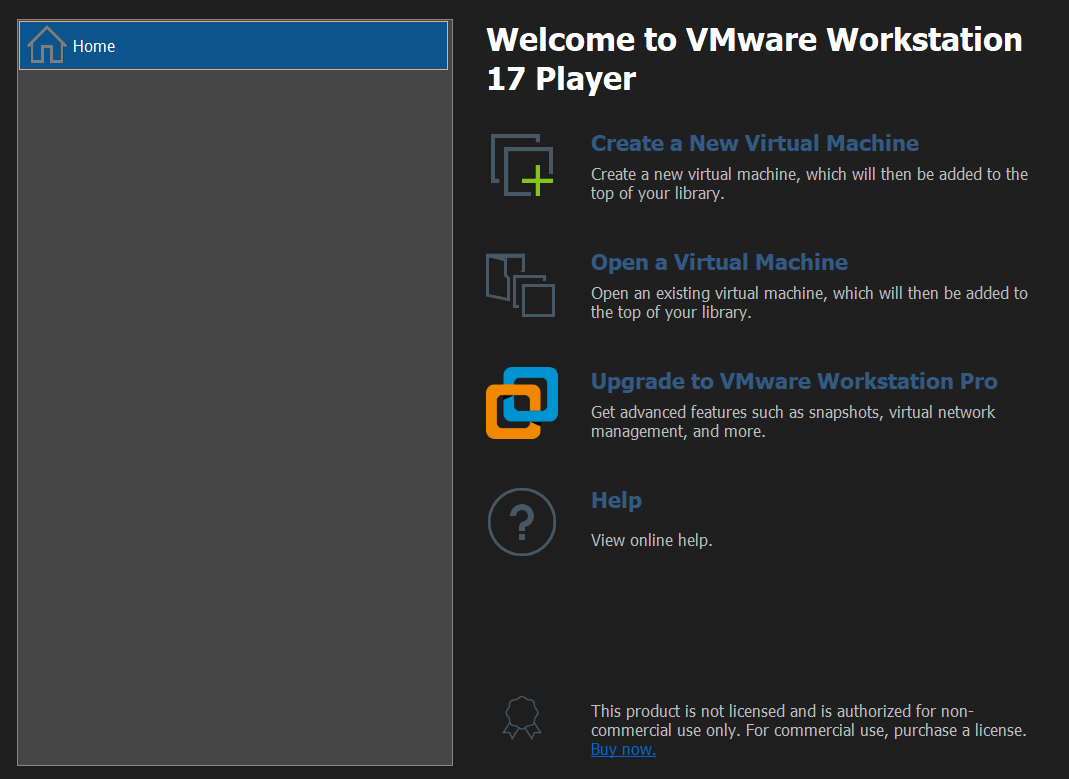
3) Adding Your Virtual Machine to VMware
Open your VM software ( In this case VMWare ) then choose “Open a Virtual Machine” ) and navigate to the folder where you downloaded the VM and open.
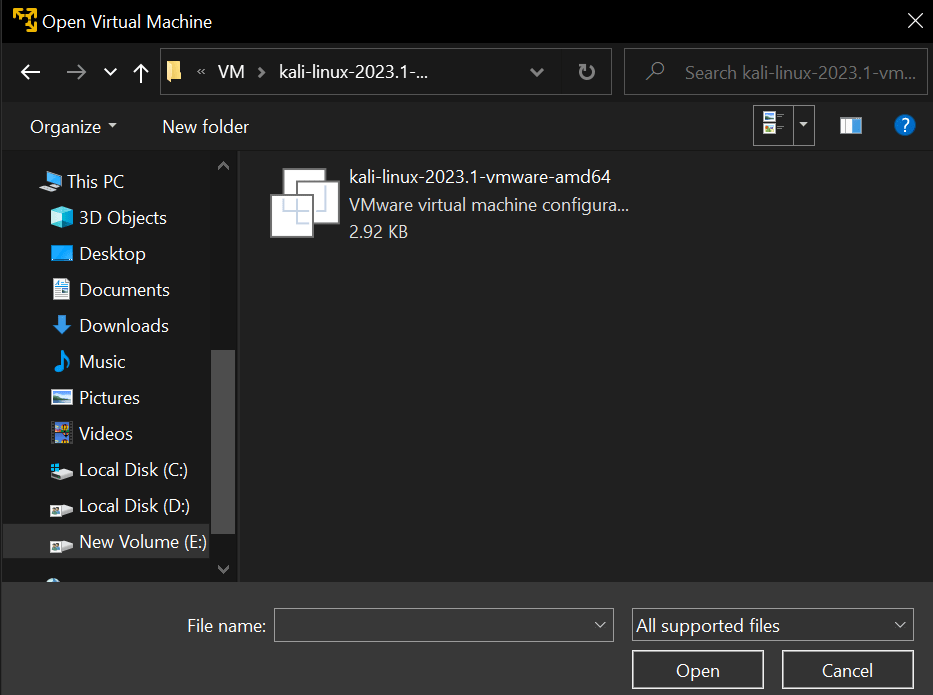
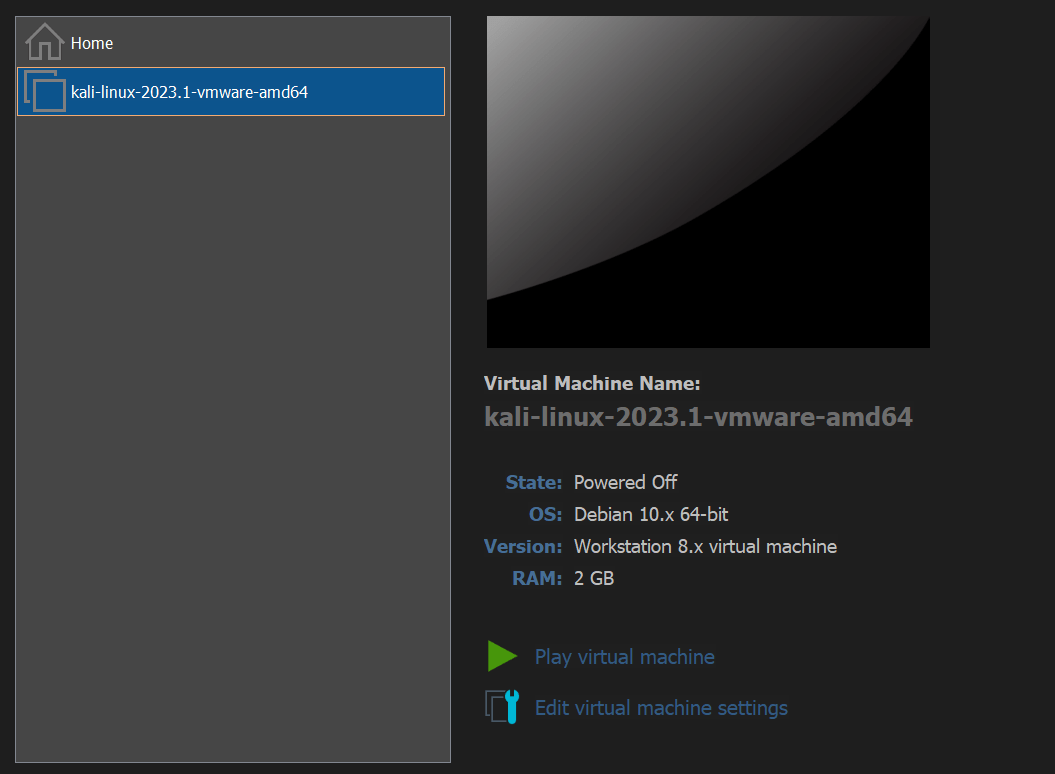
Now just click the “Play virtual machine” button and you will directly get booted into Kali Linux, there is no additional setup required
The default username and password are :
- Username: kali
- Password: kali
That’s It now, update your Linux and you can scuba dive into the world of ethical hacking and cyber security with one of the best OS for the job.
Conclusion
Installing Kali Linux on VirtualBox is a straightforward process that enables you to create a virtual environment for cybersecurity learning and practice.
By following the provided step-by-step guide and post-installation setup tips, you can confidently set up Kali Linux on VirtualBox and start exploring its powerful tools for penetration testing and security auditing.
Remember to meet system requirements, enable virtualization technology, and configure VirtualBox settings properly for optimal performance. Always practice ethical hacking and respect legal and ethical boundaries.
So, take action now! Install Kali Linux on VirtualBox and begin your journey into the fascinating world of hacking and cybersecurity. Continuously learn, practice, and stay updated with the latest tools and techniques to enhance your skills and knowledge in the field of cybersecurity.