Imagine you want to send a locked box to a friend, but you’re worried someone might intercept it. You could send the key separately, but what if that gets stolen too? This is the fundamental challenge in cryptography—how do two parties securely exchange keys over an insecure channel?
In the digital world, key exchange and key management are the backbone of secure communication. Whether you’re logging into your bank account, sending an encrypted WhatsApp message, or making an online purchase, cryptographic keys are working behind the scenes to keep your data safe.
But how exactly do we exchange keys securely? And once we have them, how do we manage them without compromising security? Let’s break it down.
Why Key Exchange Matters
Before two parties can communicate securely, they need a shared secret (a key). But if they’ve never met, how can they agree on a key without an eavesdropper stealing it?
This is where key exchange protocols come in. They allow two parties to establish a shared secret over an insecure channel—like the internet—without ever transmitting the key directly.
The Diffie-Hellman Key Exchange
In 1976, Whitfield Diffie and Martin Hellman introduced a revolutionary concept: public-key cryptography. Their Diffie-Hellman (DH) key exchange protocol solved the key distribution problem elegantly.
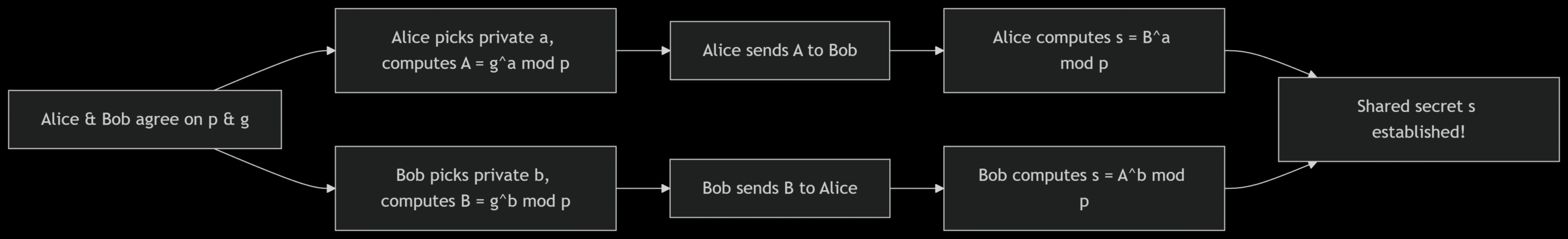
Here’s how it works (simplified):
- Alice and Bob agree on public numbers: A large prime number
pand a baseg. - Each picks a private number: Alice chooses
a, Bob choosesb. - They compute public values:
- Alice sends Bob:
A = g^a mod p - Bob sends Alice:
B = g^b mod p
- They compute the shared secret:
- Alice calculates:
s = B^a mod p - Bob calculates:
s = A^b mod p
Both end up with the same secret s, but an eavesdropper can’t easily compute it because solving a or b from A or B is computationally hard (this is the Discrete Logarithm Problem).
(Need a visual? Here’s a simple flowchart to illustrate the process.)
But Wait… What About Man-in-the-Middle Attacks?
Diffie-Hellman is brilliant, but it has a weakness: it doesn’t authenticate the parties. If Mallory intercepts the communication, she can pretend to be Bob to Alice and Alice to Bob, performing a Man-in-the-Middle (MITM) attack.
This is why modern systems combine DH with digital signatures (like in TLS) to verify identities.
Post-Quantum Key Exchange: The 2025 Landscape
With quantum computers advancing, Post-Quantum Cryptography (PQC) is no longer theoretical:
- NIST has standardized PQC algorithms like ML-KEM (formerly CRYSTALS-Kyber) for key exchange, relying on lattice-based cryptography, which resists quantum attacks 36.
- Hybrid approaches (e.g., combining DH with PQC) are gaining traction to ensure backward compatibility while transitioning to quantum-safe methods 8.
- Quantum Key Distribution (QKD) is being tested with standard fiber-optic hardware, making tap-proof communication feasible without expensive specialized equipment 5.
Key Management
Exchanging keys is just the first step. Managing them securely is equally critical. Poor key management is like having an unbreakable lock but leaving the key under the doormat.
1. Symmetric vs. Asymmetric Key Management
- Symmetric keys (AES, DES) use the same key for encryption and decryption.
- Problem: If the key is leaked, everything is compromised.
- Solution: Use secure key exchange (like DH) and rotate keys frequently.
- Asymmetric keys (RSA, ECC) use a public-private key pair.
- Problem: Slower than symmetric encryption.
- Solution: Often used just for key exchange, then switch to symmetric encryption (like in HTTPS).
2. Key Storage: Where Should Keys Live?
- Hardware Security Modules (HSMs): Tamper-resistant devices that store keys securely.
- Key Vaults (Azure Key Vault, AWS KMS): Cloud-based secure storage.
- Password Managers: For personal use, but not ideal for enterprise security.
3. Key Rotation and Revocation
Keys shouldn’t live forever. Best practices include:
- Regular rotation (changing keys periodically).
- Revocation (invalidating compromised keys).
(Remember the SolarWinds hack? Stolen certificates allowed attackers to remain undetected for months. Proper key rotation could have mitigated the damage.)
Real-World Applications
1. HTTPS (TLS Handshake)
When you visit a secure website, your browser performs a TLS handshake:
- Uses Diffie-Hellman (or ECDH) to establish a session key.
- Verifies the server’s identity with certificates.
- Switches to symmetric encryption (AES) for faster communication.
2. Signal Protocol (End-to-End Encryption)
Apps like WhatsApp and Signal use the Double Ratchet Algorithm, combining DH with forward secrecy to ensure even if one key is compromised, past messages remain secure.
3. Bitcoin and Blockchain
Cryptocurrencies rely on public-key cryptography for wallet security. Lose your private key? Say goodbye to your Bitcoin.
Common Pitfalls in Key Management
- Hardcoding keys in source code (Yes, people still do this! 🔥)
- Using weak randomness (predictable keys = breakable encryption).
- Not enforcing key expiration (long-lived keys are risky).
- Poor access controls (too many people with key access).
FAQs:
Q: Why can’t we just use asymmetric encryption for everything?
A: Because it’s slow. Symmetric encryption (like AES) is much faster for bulk data.
Q: What’s better—RSA or ECC for key exchange?
A: ECC (Elliptic Curve Cryptography) is more efficient, but RSA is still widely used.
Q: Can quantum computers break Diffie-Hellman?
A: Yes, eventually. Shor’s algorithm can solve the discrete log problem, which is why post-quantum cryptography is being developed.
Final Thoughts: The Future of Key Exchange
With quantum computing on the horizon, post-quantum key exchange methods (like Lattice-based cryptography) are gaining traction. Meanwhile, proper key management remains one of the most overlooked aspects of cybersecurity.
So next time you send an encrypted message or log into a secure site, remember—there’s a fascinating dance of keys happening behind the scenes to keep your data safe.
What’s your biggest challenge with key management? Let me know in the comments!