Cryptographic hash functions are one-way “digital fingerprints” that prove data hasn’t been tampered with, while digital signatures add an identity layer, letting us know who created (or at least approved) that data. Together they keep everyday things—bank transfers, WhatsApp backups, GST filings—unalterably secure. In this third part of our “Cryptography For Everyone” series, we’ll build on last week’s chat about integrity & authentication and tee things up for next week’s episode on cryptanalysis. Ready? ☕️
From “Did the file change?” to “Who actually signed it?”
Remember the previous post, where we hashed a plain-text message and compared digests to spot sneaky edits? Great—but that only told us something changed, not who changed it. That’s where digital signatures stroll in, arm-in-arm with the humble hash.
A quick rewind on hash functions
Think of a hash function as a Bollywood playback singer who can belt out a unique tune for any script but—crucially—no one can reverse-engineer the original lyrics from the final track ( Until you are a music psychopath 😂 ). Three properties make these functions the darlings of online security:
- Pre-image resistance – given a digest, guessing the original message is practically impossible.
- Second-pre-image resistance – you shouldn’t be able to forge a different message with the same digest.
- Collision resistance – finding any two distinct inputs that hash to the same output should require near-astronomical effort. SHA-256, for instance, still offers “near-optimal” collision resistance for its size class. (synnada.ai)
Is the system perfect? Far from it. Researchers demoed full collisions for MD5 and SHA-1 ages ago, nudging browsers like Firefox to kick SHA-1 off the public web back in 2017. (Mozilla Blog) Modern attackers now chase “hash collision” exploits targeting weaker algorithms, which is why CISOs keep sounding alarms in 2024. (LayerLogix)
HMACs: When a hash meets a (secret) key
If you salt a hash with a secret key, you get an HMAC—Hash-based Message Authentication Code. It mixes integrity with symmetric authentication, making sure only someone holding the key could have produced that digest. (Medium, Okta)
What is HOTP? | HMAC-Based OTP Explained
But salt-or-no-salt, a hash still can’t provide non-repudiation—you could always claim, “Hey, that wasn’t my server key!” To settle that argument in court, we need asymmetric magic.
Digital signatures: Your online autograph (that no one can forge—ideally)
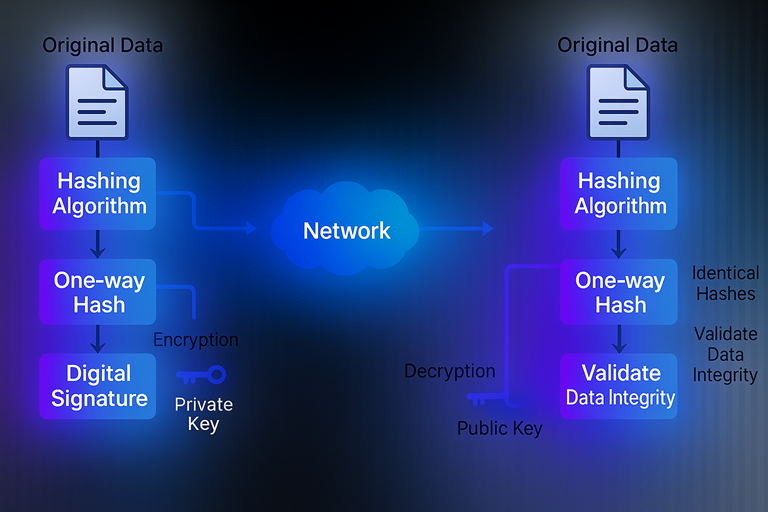
A digital signature wraps a hash with public-key crypto. You hash the document, then encrypt that digest using your private key. Anyone can decrypt it with your public key and compare digests; if they match, voila, the doc is authentic and you can’t plausibly deny authoring it.
RSA vs ECDSA
The veteran algorithm here is RSA, roomy and reliable but a tad heavyweight. Elliptic-Curve cousins like ECDSA offer the same security in far smaller key sizes—great for battery-powered gadgets and IoT sensors.
Benchmarks show ECDSA and Ed25519 verifying signatures in microseconds, where RSA takes milliseconds—handy when you are using UPI right?
And the innovation train keeps chugging: Bitcoin’s 2021 Taproot upgrade embraced Schnorr signatures for faster multisig aggregation and cheaper block space.
India’s e-signature law
Closer to home, the Information Technology Act, 2000, and follow-up rules give digitally-signed PDFs the same legal validity as pen-and-ink, provided they use certs from licensed Certifying Authorities. (Adobe Help Center, DocuSign) A 2021 Spanish court case even tossed out an alleged e-signed loan contract because the signature lacked a qualified certificate—proof that the tech and the paperwork matter. (Digt)
How the hash–signature duet actually plays out
- Hash the message (fast and input-size-agnostic).
- Sign that small hash with your private key (slow, but now tiny).
- Ship the message + signature to the recipient.
- Receiver hashes the message again, verifies the signature using your public key, and cross-checks the digests. Simple, elegant, widely used—from Aadhaar e-KYC responses to git commits.
Fun analogy: If the message is your full cricket scorecard, the hash is its brief ESPN headline, and the signature is you sealing that headline with your unique thumbprint. Anyone can reproduce the headline and compare thumbprints, but forging both? Nearly impossible.
Vulnerabilities & mitigations
- Weak hashes (think MD5, SHA-1) invite pre-computed rainbow tables and even CVEs where router firmware still stores admin passwords in MD5.
- Key mis-management—private keys on an unencrypted laptop? Might as well leave your chequebook at the dhaba table.
- Side-channel attacks—timing or power analysis can leak bits of your private key. Hardware security modules (HSMs) and constant-time libraries help.
We’ll unpack many of these attack vectors in next week’s Cryptanalysis & Cryptographic Attacks piece. Spoiler: collisions aren’t the only trick up an adversary’s sleeve.
Practical tips for security-minded devs & hobbyists
- Pick modern primitives. SHA-256/SHA-3 for hashing; ECDSA (P-256/Ed25519) or Schnorr where supported.
- Use libraries, not home-brew crypto. BoringSSL, libsodium, NaCl—battle-tested, constant-time.
- Rotate keys and phase out legacy algorithms. Mozilla’s SHA-1 sunset proves deprecation works.
- Log everything with timestamps & public cert fingerprints. That audit trail saves headaches during compliance audits (and marital audits—ask me how I know 😉).
- Educate users: a signature is only as strong as the human guarding the private key.
A note on blockchains and signatures
Every Bitcoin or Ethereum transfer gets wrapped in a digital signature, binding the transaction to the sender’s key pair and broadcasting it onto an immutable ledger. Coinbase’s developer docs call signatures the “fundamental building block” of blockchain trust. (Coinbase) Innovations like Taproot and MuSig2 show how signatures evolve to scale with real-world throughput demands. (Unchained, Phemex)
Looking ahead: From defence to offence
We’ve spent three posts emphasising how cryptography raises walls. But walls invite ladders. Next time, we’ll turn the tables and explore cryptanalysis—collision-finding, side-channels, and quantum curveballs. Understanding the offensive toolkit is the surest path to designing stronger defences.
Curious already? Chew on this: if someone could cheaply generate SHA-256 collisions tomorrow, how many blockchain transactions would survive intact? Ping me your thoughts in the comments!
FAQs
Q1: Why can’t I just encrypt the whole file instead of signing a hash?
Encrypting large files with a private key is slow and produces oversized ciphertexts. Hash-then-sign keeps the heavy math tiny and snappy.
Q2: Are digital signatures the same as electronic signatures?
Nope. An electronic signature can be a typed name or scanned scribble. A digital signature uses cryptography and offers verifiable integrity & identity.
Q3: Is ECDSA always better than RSA?
Mostly yes for performance, but RSA’s maturity and wider hardware support still matter in some legacy systems. Hybrid stacks exist.
Q4: How secure is SHA-256 today?
No practical collisions are known. Attacks focus on implementation flaws or social engineering rather than the math itself.
Q5: What happens if I lose my private key?
You lose the ability to sign (or decrypt) messages, and others can’t verify your future identity. Always keep secure backups—preferably in an HSM or hardware wallet.