There are many tools available for cyber security and digital forensic investigation. While some are open-source and free to use. These tools are maintained by a huge community of supporters contributing to the development of these free and open-source software. Many tools are used by the government as for investigation and have legal verifications. This means their findings are acceptable in a court 🤯.
We will look into multiple software, used in digital forensics and will mainly focus on the open-source, free-to-use software available for everyone at zero cost.
What Is Digital Forensic ?
Have you ever watched a movie involving a crime scene, where police or CBI tapes a crime scene and start collecting evidence that gives them a lead, later on they find the suspect by investigating the case deeply connecting all the details and evidence and forming a story haha 😂 Wasn’t it so fun to watch those movies. Okay, the point is that is what digital forensics is, we do the same thing when it comes to digital forensics it’s just all digital.
We tape the crime scene to preserve any evidence from getting tampered with, create a backup of evidence, and analyse that evidence to find some information that has the potential to lead us to the actual suspect. We Investigate all the digital aspects of a Forensic Investigation like mobiles, PC, workstations, servers, networks etc.
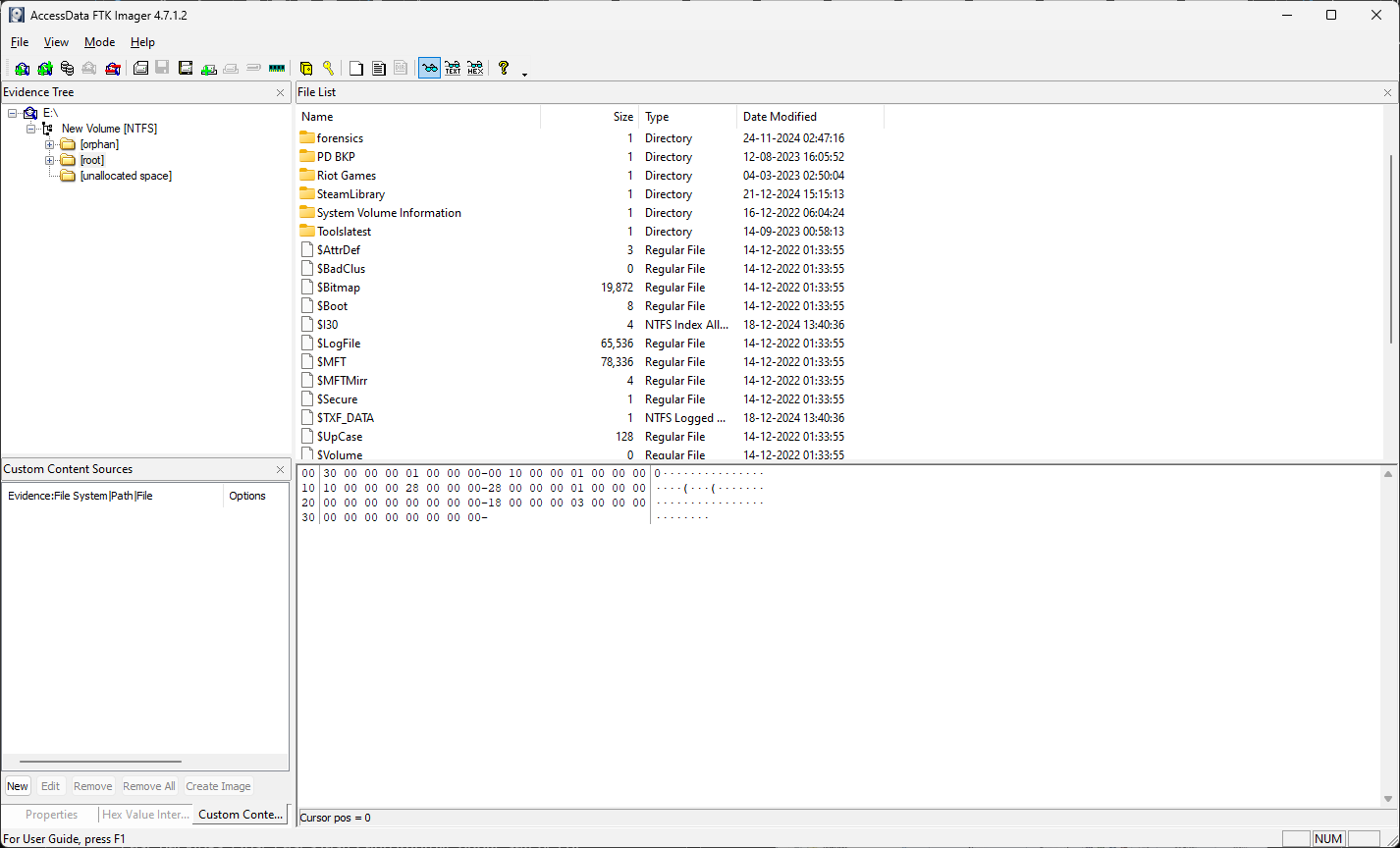
FTK Imager
FTK Imager is a free data preview and imaging tool used to acquire electronic evidence in a forensically sound manner by creating copies of computer data without making changes to the original evidence. FTK Imager is one of the best tools for taking memory dumps or creating disk images
Features
- Create Forensic Images: With FTK Imager, you can create forensic images of local hard drives, CDs and DVDs, thumb drives or other USB devices.
- Preview Data: Preview the contents of forensic images stored on a local machine or on a network drive.
- Evaluate Evidence: Evaluate computer evidence to determine if further analysis with a forensic tool such as the FTK® Forensic Toolkit is warranted.
Encase
OpenText™ EnCase™ Forensic finds digital evidence no matter where it hides to help law enforcement and government agencies reduce case backlogs, close cases faster and improve public safety. For more than 20 years, investigators, attorneys and judges around the world have depended on EnCase Forensic as the pioneer in digital forensic software to deliver reliable investigation results. ( It’s paid though )
Features
- Unmatched performance: Rely on the ability to process evidence up to 75 per cent faster than competing products, demonstrated in investigator lab testing using real-world evidence files.
- Court-accepted evidence format: Trust the evidence file formats and digital forensic evidence integrity accepted as the proven standard by court systems around the world.
- Superior efficiency: Extend the power of EnCase with a complete API that enables the automation of common investigator tasks and improves analyst efficiency.
- In-depth evidence investigation: Have confidence in investigative results with a solution that conducts disk-level analysis and parses and reconstructs data to ensure its accuracy.
Want to learn Linux and become a hacker? We’ve got you covered with Linux Basics for Hackers series. Dive into the world of hacking with the essential skills and knowledge you need to master Linux. From the basics to advanced techniques, this series will guide you every step of the way.
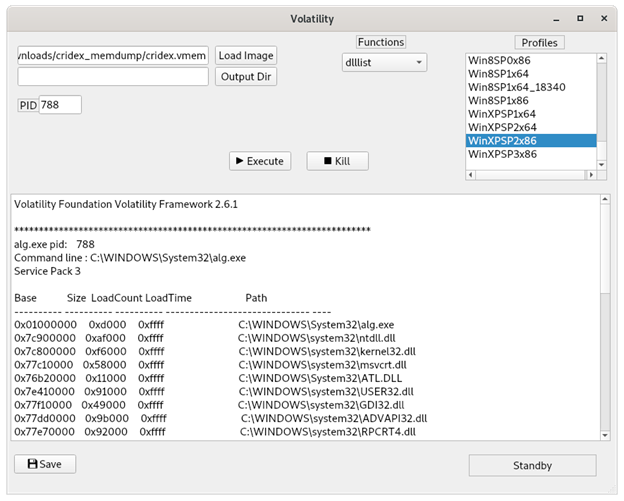
Volatility
Crafted by the Volatility Foundation, this open-source framework is designed for deep analysis of volatile memory in systems. It’s the product of a dedicated team of forensic and security experts, evolving from Volatility2 to meet the challenges of modern digital forensics. It is a CLI application but there is a GUI for volatility known as volatility workbench. The image below is of volatility workbench but if you prefer CLI go to volatility release.
Features
- Active and hidden processes, indicating possible system breaches.
- Network activities and connections that could point to malware communication.
- Command execution history, potentially exposing actions by malicious entities.
- Loaded kernel modules, identifying anomalies or rootkits.
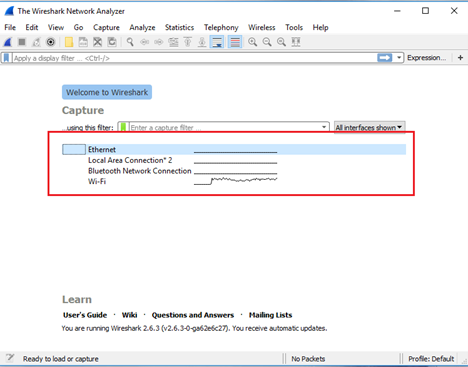
Wireshark
Wireshark is the world’s foremost network protocol analyzer. It lets you see what’s happening on your network at a microscopic level. It is the de facto ( often de jure) standard across many industries and educational institutions.
Features
- Deep inspection of hundreds of protocols, with more being added all the time
- Live capture and offline analysis
- Standard three-pane packet browser
- Multi-platform: Runs on Windows, Linux, OS X, FreeBSD, NetBSD, and many others
- Captured network data can be browsed via a GUI, or via the TTY-mode TShark utility
- The most powerful display filters in the industry
- Rich VoIP analysis
Tcpdump
tcpdump is a data-network packet analyzer computer program that runs under a command line interface. It allows the user to display TCP/IP and other packets being transmitted or received over a network to which the computer is attached. Distributed under the BSD license, tcpdump is free software.
Features
- Packet Capture: Captures live network traffic for analysis.
- Filtering: Uses powerful filters (BPF syntax) to capture specific packets (e.g., IP, port).
- Save & Replay: Saves captured packets in
.pcapformat for later analysis. - Protocol Support: Analyzes a variety of protocols, including TCP, UDP, ICMP, and HTTP.
- Interface Selection: Captures traffic on specific network interfaces.
- Promiscuous Mode: Captures all network packets, not just those addressed to the host.
These were the most basic tools that you should learn when diving into digital forensics. There are many articles, and videos available online that teach about digital forensics utilizing these tools and many others I have not covered in this blog. So, what are you waiting for go get your hands dirty and learn something new 😄.